How To Decrypt Apco 25 Encryption Programs
Introduction to P25 Encryption. Topic Progress: ← Back to Lesson. Encryption in radio communications enables secure communication between parties and is achieved by loading the same key into all radios in a group. The key is like a secret number or password that must be known in order to decrypt the call. APCO PROJECT 25, STATEMENT OF REQUIREMENTS, (P25 SoR), March 3, 2010, Section 4.1.1.1 AES Encryption Must be Used by the Federal Government “5.1 Encryption Services - Several encryption algorithms are available for use with P25 systems. The oldest algorithm, for which there are P25 standards documents, is Data Encryption Standard (DES).
I want to crypt and decrypt one file using one password.
How can I use OpenSSL to do that?
jww8 Answers
mikemaccanaShort Answer:
You likely want to use gpg instead of openssl so see 'Additional Notes' at the end of this answer. But to answer the question using openssl:
To Encrypt:

To Decrypt:
Note: You will be prompted for a password when encrypting or decrypt.
Long Answer:
Your best source of information for openssl enc would probably be: https://www.openssl.org/docs/apps/enc.html
Command line:openssl enc takes the following form:
Explanation of most useful parameters with regards to your question:
Additional Notes:
Though you have specifically asked about OpenSSL you might want to consider using GPG instead for the purpose of encryption based on this article OpenSSL vs GPG for encrypting off-site backups?
To use GPG to do the same you would use the following commands:
To Encrypt:
To Decrypt:
Note: You will be prompted for a password when encrypting or decrypt.
Encrypt:
Decrypt:
For details, see the openssl(1) docs.
Update using a random generated public key.
Encypt:
Decrypt:
I have a full tutorial on this at http://bigthinkingapplied.com/key-based-encryption-using-openssl/
jeanMotorola Apco 25 Radios
Note that the OpenSSL CLI uses a weak non-standard algorithm to convert the passphrase to a key, and installing GPG results in various files added to your home directory and a gpg-agent background process running. If you want maximum portability and control with existing tools, you can use PHP or Python to access the lower-level APIs and directly pass in a full AES Key and IV.
Example PHP invocation via Bash:
This outputs:
You could also use PHP's openssl_pbkdf2 function to convert a passphrase to a key securely.
DO NOT USE OPENSSL DEFAULT KEY DERIVATION.
Currently the accepted answer makes use of it and it's no longer recommended and secure.
It is very feasible for an attacker to simply brute force the key.
PBKDF1 applies a hash function, which shall be MD2 [6], MD5 [19] or SHA-1 [18], to derive keys. The length of the derived key is bounded by the length of the hash function output, which is 16 octets for MD2 and MD5 and 20 octets for SHA-1. PBKDF1 is compatible with the key derivation process in PKCS #5 v1.5. PBKDF1 is recommended only for compatibility with existing applications since the keys it produces may not be large enough for some applications.
PBKDF2 applies a pseudorandom function (see Appendix B.1 for an example) to derive keys. The length of the derived key is essentially unbounded. (However, the maximum effective search space for the derived key may be limited by the structure of the underlying pseudorandom function. See Appendix B.1 for further discussion.) PBKDF2 is recommended for new applications.
Do this:
openssl enc -aes-256-cbc -pbkdf2 -iter 20000 -in hello -out hello.enc -k meow
openssl enc -d -aes-256-cbc -pbkdf2 -iter 20000 -in hello.enc -out hello.out
Note: Iterations in decryption have to be the same as iterations in encryption.
Iterations have to be a minimum of 10000.Here is a good answer on the number of iterations: https://security.stackexchange.com/a/3993
Also... we've got enough people here recommending GPG. Read the damn question.
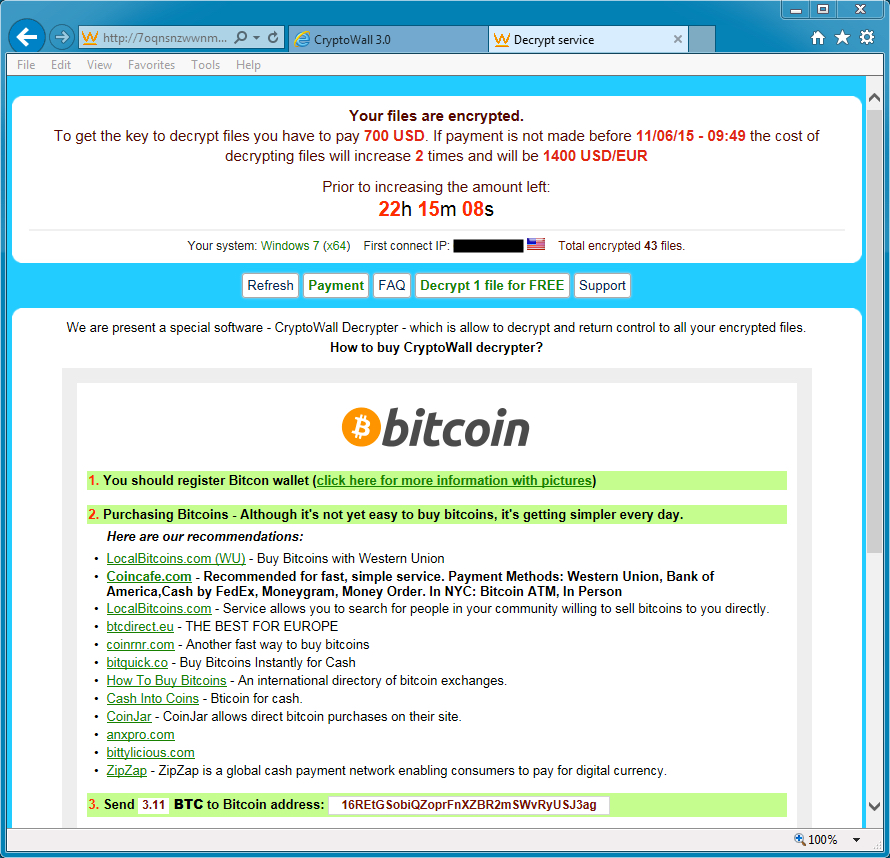
There is an open source program that I find online it uses openssl to encrypt and decrypt files. It does this with a single password. The great thing about this open source script is that it deletes the original unencrypted file by shredding the file. But the dangerous thing about is once the original unencrypted file is gone you have to make sure you remember your password otherwise they be no other way to decrypt your file.
Here the link it is on github